your passion is C++, our passion is Clean Code
Sonar static analysis helps you build and maintain high-quality C++ code. Covering popular build systems, standards and versions, Sonar elevates your coding game while keeping vulnerabilities at bay.
Write Clean C++
static code analysis tools for your C++
Utilize static code analysis to find issues in C++ such as bugs, code smells & security vulnerabilities. Use the Sonar language analyzer with hundreds of rules to evaluate your code and ensure the security, reliability and maintainability of your software.
Sonar static analysis helps you build and maintain high-quality C++ code. Covering popular build systems, standards and versions, Sonar elevates your coding game while keeping vulnerabilities at bay.
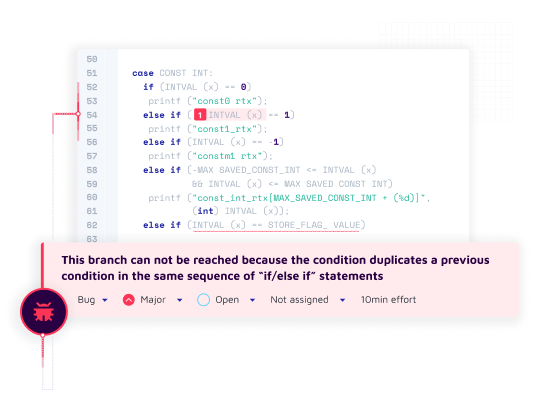
Tool-checkable rules extracted from expert guidance on how to write modern, robust code.
Rules to detect vulnerabilities stemming from known OWASP & CWE Top 25 guidelines.
Your safety-critical software benefits from Sonar. After actively contributing to the MISRA C++2023 guidelines, Sonar offers coding guidance from the IDE onwards for your mission-critical applications. Ensure the code you write today is clean and secure, and your teams are aligned around a common set of MISRA C++ 2023-specific coding guidelines.
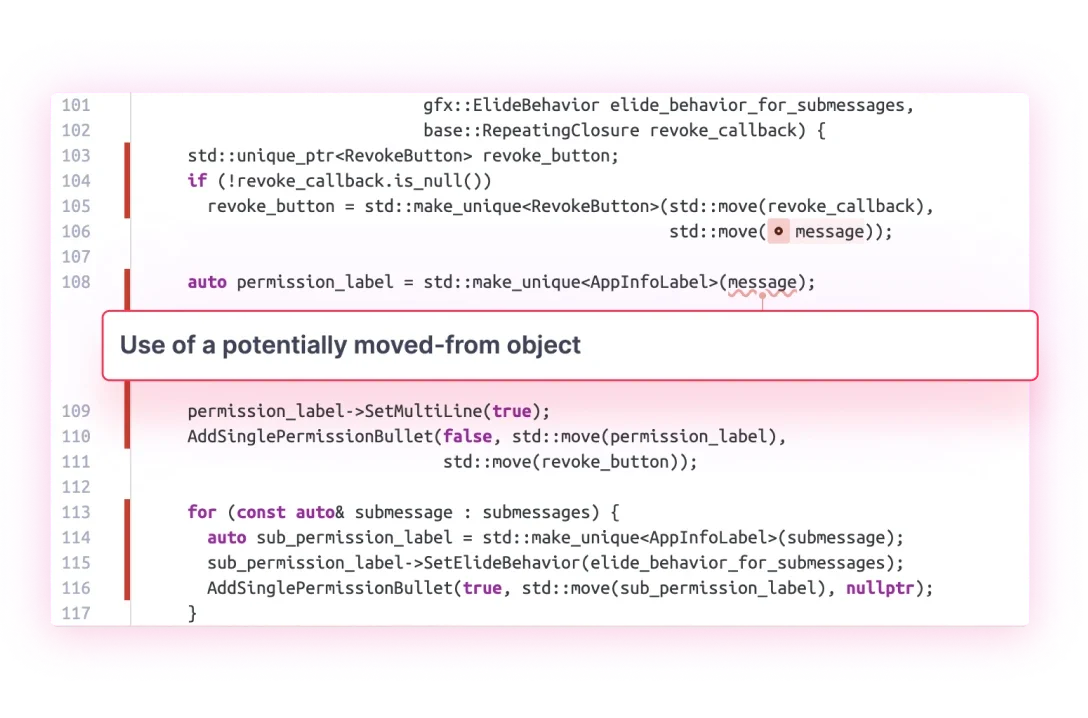
It all comes from a powerful static analysis engine that we constantly refine. SonarQube employs advanced rules along with smart, exclusive static code analysis techniques to find the trickiest, most elusive issues, code smells, and security vulnerabilities.
Download SonarQube NowDeep static analysis of your code through symbolic execution, path sensitive analysis & cross-function/cross file analysis.
Issue contextualization with secondary locations highlighted and clear remediation guidance helps you understand and construct a fix.
Automatic pull request analysis with results decorated in your favorite DevOps platform so you stay in the zone.
SonarQube is easy to onboard and has a wide variety of languages that are supported.
Prahlad Ram, DevOps Technical lead @ Verse
Sonar brings Clean Code to where your code lives. Sonar is tightly integrated with your CI/CD workflow to feed you the right info at the right time and place.
SonarLint in your IDE is your first line of defense for keeping the code you write today clean and secure. Issues are raised in-line with clear rule descriptions and guidance.
With SonarLint, the impact is immediate and no configuration is required. You learn from the real-time feedback provided and quickly resolve issues with contextual guidance and automatic Quick Fixes.
MISRA C++ 2023 rules now available!
SonarLint is available from your IDE marketplace:
Visual Studio | VS Code | JetBrains | Eclipse
Automatically analyze Pull Requests and feature branches with the results decorated in the DevOps platform of your choice.
Your team can share rule configurations and exclusions across projects and coalesce on a shared definition of excellence. The project Quality Gate is visible to everyone and the releasabity status is clear.
SonarCloud tightly integrates with these popular platforms:
GitHub | Bitbucket | Azure DevOps | GitLab
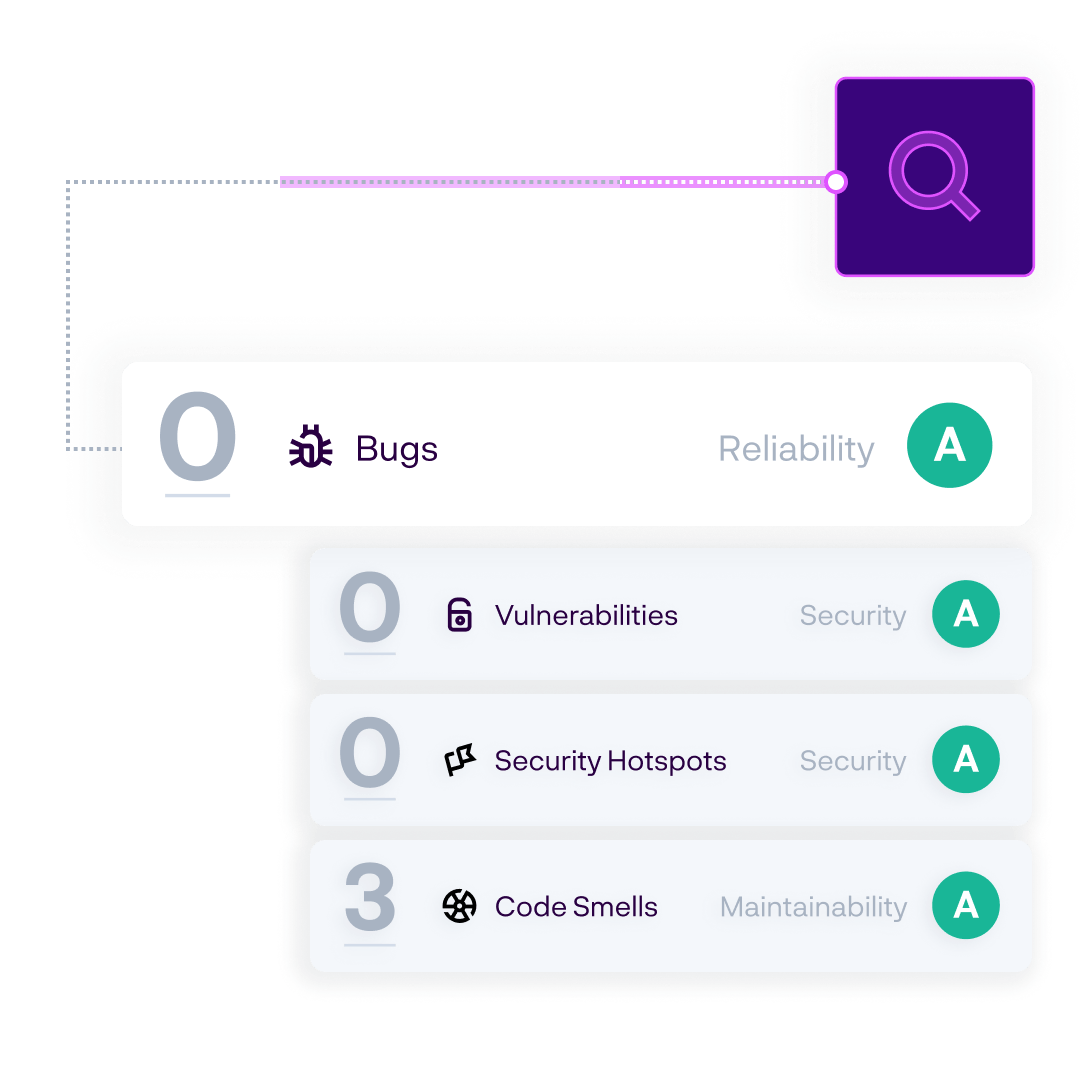
As a developer, your priority is making sure the C++ code you write today is high quality and secure. The SonarQube user interface highlights the health of your New Code (changed or added) so you’ll clearly know when your code is solid.
Out of the box, the Sonar Quality Gate clearly signals whether your commits are clean and your projects are releasable. A Quality Gate coalesces the team around a shared vision of quality. Everyone knows the coding standard of excellence and whether it’s being met.